| PenProtect Handbuch |
| (Diese Seite ist nur auf Englisch erhältlich) |
Index
- Introduction.
- PenProtect main features.
- Detailed description of some PenProtect functions.
- How to use PenProtect.
- Frequently Asked Questions (F.A.Q.).
The purpose of PenProtect is to protect the files located in your Flash Drive, Flash Memory, Pen Drive or USB Flash Drive device.
A Pen Drive (key USB stick pen or USB) or Flash Drive is a portable mass storage inserted within USB port of any personal computer. Thanks to its small size, absence of mobile mechanisms (unlike common hard disk) and affordable price, the Pen Drive (and the Flash Memory) is becoming increasingly popular among consumers.
Due to its increased popularity, prices have reduced and GByte storage has increased. Unfortunately, users can often forget their Pen Drive or Flash Drive in a computer, allowing other users to access their personal data. PenProtect is meant to secure your data in cases such as these.
The PenProtect program was created with the purpose to protect the files located in your Flash Drive or Pen Drive and does not require any installation on a PC.
The program PenProtect has been developed by EasyLine.
For further information, visit www.penprotect.com or write to
support@penprotect.com.
2. PenProtect main features.
- PenProtect requires no installation. It is a single file located in the home folder of your Flash Drive, Flash Memory or Pen Drive.
- Data protection is performed using an AES encryption (256-bit key) without changing the Flash Drive, Pen Drive or Flash Memory partition.
- Two protection levels (Partial and Total).
- Ability to encrypt or decrypt only required files.
- Immediate use of PenProtect.
- No size limit of encrypted files.
- Unique and individual protection for every Flash Drive, Flash Memory or Pen Drive.
- PenProtect comes with an internal manual that can be viewed with no Internet connection.
- Program PenProtect comes in many languages.
- Free technical assistance.
3. Detailed description of some PenProtect functions.
 |
PenProtect works by running the file "PenProtect.exe" located within its Flash Drive or Pen Drive. The file occupies very little space on your device: about 1 MB! |
 |
In order to execute PenProtect, enter your Password (repeat for security in the field Confirm), then press the button to run data protection. |
 |
Files saved in your Flash Drive or Pen Drive are encrypted using a new algorithm, AES with a 256-bit key, chosen also by the Government of the United States of America. For more information on the methodology used and AES security please refer to page in Wikipedia.
|
 |
To decrypt files run PenProtect, enter the Password and press the button to decrypt them.
|
 |
Data remains safe during the encryption and decryption process. After this process is finished, the option to restore the data is available.
|
 |
Your own Flash Drive or Pen Drive is individually unique. The same encrypted files cannot be decrypted by a user utilizing PenProtect with your same password! This concept is fully explained in the F.A.Q.
|
 |
The integrity of your data (Flash Drive or Pen Drive) is continually being monitored by PenProtect. |
 |
To protect the data, there are two possibilities: a "Partial" or a "Total" protection. The "Total" protection option is extremely innovative. Before and after encryption, it analyzes each Flash Drive in order to eliminate any file traces. During this process PenProtect program uses a specifically created algorithm. The "Partial" protection option requires about half the time of the "Total" one, but your data protection is not 100% secure.
|
 |
Using PenProtect you can secure your data saved in your Flash Drive, Pen Drive, Flash Memory or any memory made with USB Flash drive. For more information, please see the FAQ page ( question 1, question 3). Below there is an image containing most of the formats supported by PenProtect:

|
4. How to use PenProtect
After installing PenProtect you will have a file titled "penprotect.exe" automatically placed in your Flash Drive or Pen Drive. We suggest to copy this file and place it in a safe place. If lost, the file can be obtained by:
using the installation program;
requesting the file by e-mailing PenProtect support (support@penprotect.com);
in the Customer Area of the site www.penprotect.com. Use the Username and Password you received in the e-mail at the time of purchase.
Before running PenProtect you must copy all the files within your Flash Drive or Pen Drive to either "My Computer", "Explorer" or any other program that is able to copy/move files. In order to run PenProtect you should launch the file "penprotect.exe" directly from your Flash Drive or Pen Drive:
or from the PenProtect icon found on your Desktop:
This icon will appear on your Desktop only after using PenProtect for the first time.
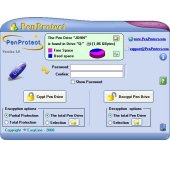
After running the "penprotect.exe" file, the following screen will appear (the image is reduced):
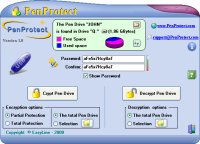
By scrolling your mouse over the buttons, an explanation of each icon will appear. For example:
The following graphic description explains the functions of PenProtect:
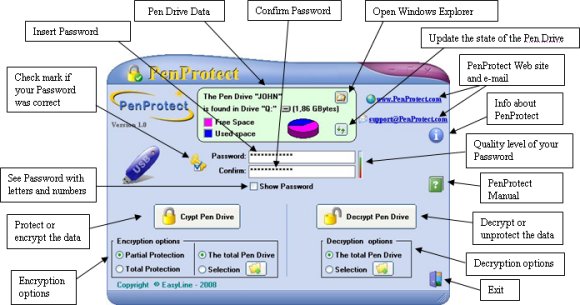
(Click on the image to enlarge)
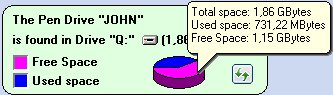
In the middle of the top figure there is a description of your Flash Drive or Pen Drive: name, size and total space occupied.
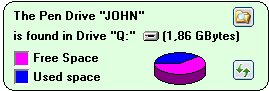
In this case, the Flash Drive is called "JOHN" and is located in the drive "S" of the Computer. The size of Flash Drive is 1.86 GBytes or around 2 GBytes. The graphic image below indicates that the Flash Drive has about 3/5 free space. To
get an accurate estimation of the available space, just place your mouse over the cake shaped diagram:
Use the button (highlighted by a blue circle):
to open Windows Explorer in a new window.
Use the button (highlighted by a red circle):
to update the status of your Flash Drive or Pen Drive.
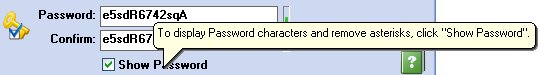
Just below you can see the "Password" and "Confirm" space in which you must enter and confirm your Password. When the words match, you get the image of a golden key, located on the left, which has a small blue checkmark. This indicates that your password is correct.
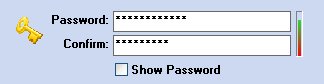

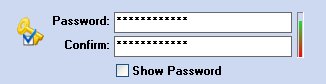
To see the password characters (eliminate asterisks) click the Show Password option:
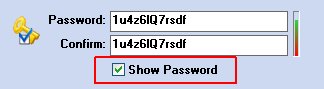
Passwords should be chosen carefully. We recommend to insert at least 6 characters among the following:
ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz
0123456789$%!/\()=?^*-#[]§@£&
Use a mixture of characters (i.e. putting some letters and at least a couple of numbers). Do not use characters (such as period ".") not found in the above list. The operational system is limited and it will not allow you to use other characters.
To get an estimation of your password security level you can have a look at the small bar on the right of the "Password".
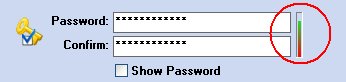
The greener the level, the safer your password will be. We provide a maximum of 30 characters.
In the central part of the screen there are two buttons used to encrypt (protect) or to decrypt (unprotect) data or files in your Flash Drive or Pen Drive.
Before pressing the encryption or decryption button, you can view protection levels. Under the encryption button there are the following options:
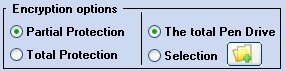
PenProtect provides two types of protection for encryption:
- The "Partial Protection" option requires about half the time of the "Total" one, but your data protection is not 100% secure. A hacker, however, admitted to the Flash Drive for a reasonable time, may be able to read the contents of some files.
- The "Total Protection" option is extremely innovative. Before and after encryption, it analyzes each Flash Drive in order to eliminate any file traces. During this process PenProtect program uses a specifically created algorithm. (Hacker safe!)
You can protect files on your Flash Drive using both options and the decryption process will not be affected by your choice.
The other option allows you to make a selection of the file protected. You can encrypt all data contained within your Flash Drive or only specific files or folders.
In order to select the files or folders you can use the appropriate button (shown below with a red square):
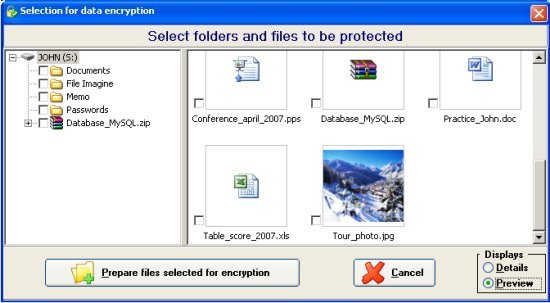
that can be accessed with the following screen:
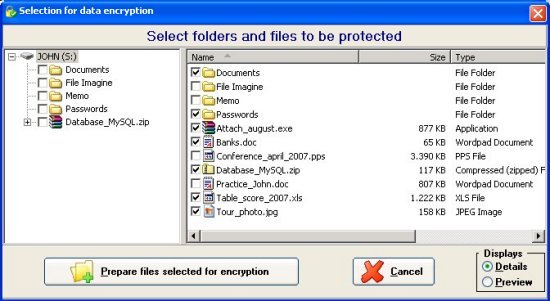
The screen lists only the folders within the Flash Drive or Pen Drive. You must select the files and folders to be protected (as shown in the previous image). By using the small box on the lower right,
you can view all the files by pressing "Preview":
After selecting appropriate folders and files, press:
If you have selected at least one file, then the option will change automatically:
After setting the Options you want, press the button

This will start the process of data encryption.
A screen similar to the following will be shown:
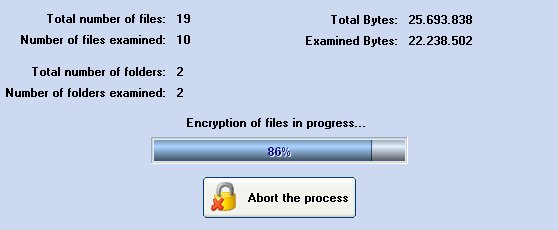
This table indicates the amount of data being encrypted.
In order to cancel the encryption process, press the button:

You might have to wait some time for the Flash Drive to restore to its original setting.
At the end of the process the following screen will appear:
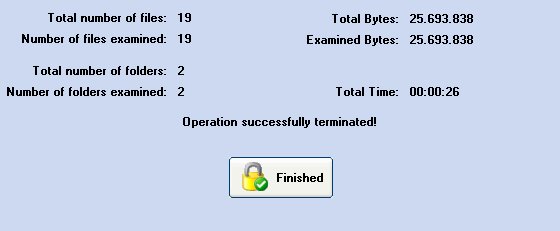
This screen displays a detailed account of the encryption process.
At this point you can take the Flash Drive out the computer (as described by the manufacturer).
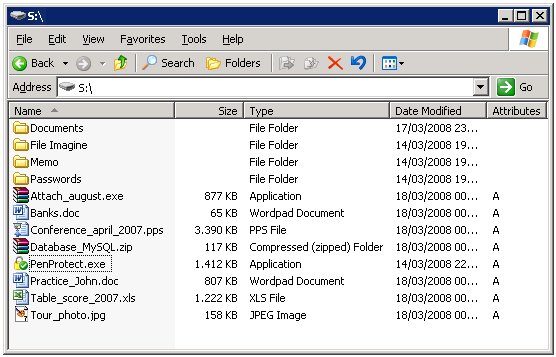
After the encryption process, it will appear that the files and folders have strange names and make no sense. Below are two screens: before and after encryption.
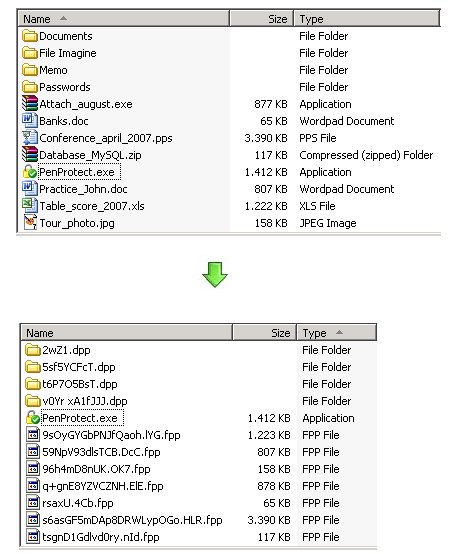
This is the effect of running PenProtect. It is not only encrypts the file content, but also the file name and folders. This makes it safe to insert personal data when naming files.
In addition, each file loses its characteristics. For example, a typical Microsoft Word file that has a .DOC extension can no longer be recognized as a Word document after encryption. A file .EXE, which is the usual extension for file applications, can also no longer be executed after encryption. Consequently, the PenProtect protection is particularly efficient.
After encryption, every protected file has the extension .FPP (File PenProtect) and every folder has a special extension .DPP (PenProtect Directory).
It is not possible to encrypt a file or folder more than once.
As you can see from the previous image PenProtect program file (penprotect.exe) has not been encrypted. It will later be used to decrypt files within Flash Drive or Pen Drive.
After the data encryption, the total free space in your Flash Drive or Pen Drive will have only been reduced a little. This is a normal consequence of using the algorithm (AES) to encrypt data.
To decrypt the data you have two options:
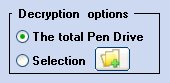
On the Flash Drive or Pen Drive you can decrypt all the files and folders or only the data (files and/or folders) selected. To select data, press the button highlighted below:
Sometimes you may decrypt or unprotect only a few files. This option is very useful because it allows you to have the desired data only after a few seconds.
It may be difficult to find the file to decrypt because its name was encrypted earlier. To find the desired file, you can look at the file size dimensions.
Inside the Flash Drive or Pen Drive it is possible to have data that is both encrypted and not encrypted.
5. Frequently Asked Questions (F.A.Q.)
Q: What are the exact steps for using PenProtect?
A: Steps for encryption:
1) Copy on your Flash Drive or Pen Drive the files that must be protected.
2) Run "penprotect.exe".
3) Insert your Password and rewrite it in the "Confirm" field.
4) Choose the type of protection (Partial or Total).
5) Choose whether protect all files or a selection of files.
6) Press the button "Crypt the Pen Drive" and wait for the end of the operation.
7) Quit PenProtect.
8) Remove the Flash Drive or Pen Drive from your PC using the "Disconnect or remove a hardware device".
Steps for decryption:
1) Insert the Flash Drive or Pen Drive and run "penprotect.exe".
2) Enter your Password.
3) Choose whether to unprotect all files or a selection of files.
4) Press the button "Decrypt the Pen Drive" and wait for the end of the operation.
5) Close PenProtect. Now the Flash Drive or Pen Drive is ready to be used.
Q: How do I know if the Flash Drive or Pen Drive has been protected?
A: Look at file and folder names under "My Computer". If the Flash Drive or Pen Drive was protected, then all the names will be written using characters such as "au6fGBW9QEoPQiYgXZOQ3" and are unreadable. Furthermore, the encrypted files have the extension .FPP (File PenProtect) and folders with a special extension .DPP (PenProtect Directory). (See also this image).
Q: Is the encryption process safe?
A: The type of encryption used within PenProtect is extremely efficient. The encryption technique is called AES (Advanced Encryption Standard) using a 256 bit key and a special algorithm that, for security reasons, will not be revealed here. The transaction also contains two additional encryption processes of protection, invisible during the operation, but extremely effective to further safeguard the data. It is precisely these two processes that make PenProtect a unique program regarding data security. For more information on AES, which is currently used as a standard by the United States Government and numerous banks, one can refer to the following page: Advanced Encryption Standard in Wikipedia.
Q: Can I use PenProtect even for the hard disk?
A: No, PenProtect can be used only on devices known as USB Flash Drive. The following image contains most of the devices currently on the market:

Before purchasing PenProtect, you can download the demo version (Download Page). If the demo version of PenProtect works on your Flash Drive, Pen Drive, Flash Memory or Device the full version will be equally successful. The purchase is not recommended if there were problems while executing the demo version.
Q: After the execution of the protection by PenProtect can I retrieve data using specific programs "Undelete" files? Does PenProtect protect against programs "Undelete"?
A: The software technology used for PenProtect was also designed to avoid data recovery programs such as "Undelete". PenProtect has carried out numerous tests using popular data recovery programs currently on the market (3.0 Handy Recovery, Recover My Files 3.90, Back2Life 2.5, File Rescue Plus 3.0, R-Undelete 3.0, FinalRecovery 2.2.4, Undelete 4.0, File recover 6.0). None of these programs were able to recover the original file.
Q: What happens if I forget my Password?
A: For a complete data protection there is no backdoor that can restore the data or find your Password. For this reason, it is strongly recommended to save your data before using PenProtect and to write down or remember your Password.
Q: What happens if I format my Flash Drive or Pen Drive?
A: All data in Flash Drive or Pen Drive will be permanently erased.
Q: What is a good Password?
A: PenProtect requires a Password from a minimum of 6 up to a maximum of 30 characters. It should include both letters and numbers. To get an estimation of the quality of the password that was entered, there is a small colored bar to the right. In this part of the manual there is additional information.
Q: Is PenProtect a safe program?
A: We have tried to create a product that can prevent any malfunction by carrying out numerous tests on different files and devices. We recommend that you always keep a safe copy of your data. This is meant not only for PenProtect actions, but also because the Flash Drive or Pen Drive can easily have hardware problems. PenProtect is provided "as is" (AS IS) and should be used at your own risk. We can not guarantee there will be no damage.
Q: With what operating systems does PenProtect works?
A: The current version of PenProtect works only on Microsoft Windows (95, 98, Me, 2000, XP, NT4, 2003 and Vista).
Q: How much time does it take PenProtect to protect a 512 Mbytes Flash Drive or Pen Drive?
A: The speed of protection depends heavily on the speed of read-write data own Flash Drive or Pen Drive. Moreover, the speed also depends on the brand. For a Pen Drive from 512 MBytes the speed is about 4 MBytes/s to be written and about 7 MBytes/s to be read and if the Pen Drive is completely full, PenProtect takes about 4 minutes to protect data and approximately 3 minutes to unprotect them. The Flash Drive or Pen Drive are on the market from the beginning of 2008 and that some have a capacity of over 1 GByte and can reach speeds close to 20-30 MBytes/s. With these new Flash Drive or Pen Drive, PenProtect takes less than 30 seconds to protect 512 Mbytes of data.
The amount of time for protection depends on the speed device. There is no program on the market that can protect data on a Flash Drive or Pen Drive in few seconds.
It is not absolutely necessary to protect or unprotect all the contents of your Flash Drive. PenProtect provides the option to protect and unprotect only the desired files. The PenProtect program was created to reduce the amount it takes to protect files, while still providing the same reliabilty and security of data.
Q: Does the file "penprotect.exe" remain on my Flash Drive or Pen Drive even after the encryption process?
A: Yes. During the operation, "penprotect.exe" is not encrypted allowing it to be used for the decryption process. (See also this image).
Q: What happens if I enter an incorrect Password when trying to decrypt my files?
A: PenProtect will tell you that your Password is wrong. After three failed attempts, you will be forced to exit PenProtect.
Q: I tried to copy the file "penprotect.exe" on another Flash Drive or Pen Drive, but the program does not start!
A: PenProtect only works on the registered Flash Drive or Pen Drive. If for some reason it is no longer possible to use the original Pen Drive, you can obtain a new registration. You can contact the staff of PenProtect by e-mail address support@penprotect.com.
Q: I have seen that PenProtect has created an icon on my Desktop. What is it for?
A: The icon on your Desktop serves as a shortcut to the PenProtect program.
Q: How much space does PenProtect take on my Flash Drive or Pen Drive?
A: The PenProtect program consists of the file "penprotect.exe" and takes aproximatively 1 MByte. See for example the following image. The file contains procedures for encryption and decryption, control screens and the manual.
Q: Does PenProtect work on all USB ports?
A: The PenProtect program supports standard of 1.0 (1.5 speed Mbit/s), the standard 1.1 (speed 12 Mbit/s) and 2.0 (speeds up to 480 Mbit/s). The new USB 3.0, released in late 2007, has not been tested yet with PenProtect.
Q: Does PenProtect encrypt data in the same way on every single Flash Drive or Pen Drive?
A: No. It uses a particular system that encrypts identical data in different ways. Even if both users have the same exact password and file name and contents, they will be encrypted to appear differently. From the images below you can make a visual comparison of the difference between the encryption "Q: Flash Drive" (left) and "S: Flash Drive" (right). The two screens at the top indicate the files before encryption; those at the bottom indicate files after encryption. As you can see, through two red squares, the same data is encrypted in different ways:
(Click on the image to enlarge)
Q: I accidentally formatted my Flash Drive and I erased the "penprotect.exe" file. How can I retrieve it?
A: Enter the Username and Password provided at the time of purchase (via e-mail) in the Customer Area of
www.penprotect.com. After a few moments, the file penprotect.exe will appear on your Flash Drive or Pen Drive.
Q: Can I use PenProtect on a memory card contained in a USB card reader?
A: Yes, because the device is recognized by the computer as a USB Flash Drive. In this image there are some USB card readers:

It would be valid to reread this previous question.
Q: Is there a Byte size limit of the Flash Drive or Pen Drive?
A: No, PenProtect has no limit!
Q: Can I transfer the licence PenProtect from one Flash Drive, Flash Drive or Pen Drive to another?
A: Yes. Just send an e-mail to the PenProtect staff at support@penprotect.com and we will enable the new registration.
Q: Does PenProtect protect any type of file? Even hidden or system files?
A: Yes. PenProtect protects all your files. In the next image there are some hidden or system files that have been protected:
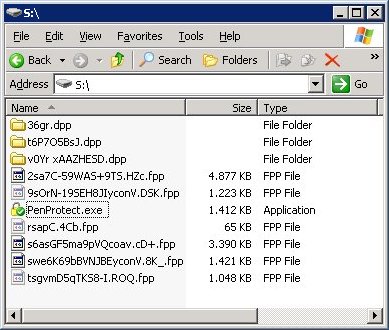
Q: Do I need an Internet connection to install PenProtect?
A: Yes, PenProtect installation requires an Internet connection. During regular use of PenProtect, no Internet connection is necessary.
Q: I have changed the e-mail with which I purchased PenProtect. How can I report it?
A: Using the Username and Password provided at the time of purchase, you can enter in the Customer Area of www.penprotect.com and change your e-mail.
Q: How do I format my Flash Drive?
A: The Flash Drive can be independently formatted using the FAT or FAT32 file system.
Q: How can I contact the staff of PenProtect?
A: For technical support, please contact us:
 |
|
 |
|
via phone: +39.06.82000285 |
|
|